Quick Answer: The best way to secure a home office is to combine strong cybersecurity with physical safeguards. Essential steps include securing your router, using a VPN, enabling multi-factor authentication, encrypting data, and protecting IoT devices. Small business security at home requires a layered approach to safeguard both company data and family privacy.
If you run your business from home, your office is the hub where sensitive company data and family privacy collide. Strong home office security isn’t optional; it’s what shields your business from costly cyberattacks while keeping your loved ones safe from digital intrusions.
The U.S. Census Bureau reports that remote work has surged, with over 27 million people now working primarily from home, yet most setups are still wide open to threats. IBM’s 2024 Cost of a Data Breach Report puts the average global breach at $4.88 million, with incidents tied to remote work costing even more.
For entrepreneurs and professionals balancing both personal and professional responsibilities, investing in small business security at home is a necessity for protecting trade secrets, financial stability, and your family’s online safety.
Table of Contents
Key Takeaways
- Home office security protects both sensitive business data and family privacy, making it essential for remote professionals and entrepreneurs.
- Network security is the foundation, with router protections, WPA3 encryption, and segmentation critical for blocking intrusions.
- VPNs, password managers, and multi-factor authentication form the backbone of identity and access management for remote workers.
- Data protection requires encryption, business-grade cloud storage, and the 3-2-1 backup rule to reduce the risk of breaches and loss
- Communication platforms, from email to video conferencing, are prime attack surfaces and require layered protections against phishing and impersonation.
- Physical and IoT security are equally important, with device locks, smart monitoring, and parental controls reducing both digital and in-home risks.
- Take action today with Batten’s bundled solutions to simplify home office security and safeguard your business and family.
Network Security: Your Digital Foundation
Your home network is the backbone of both business operations and family safety, yet most setups remain dangerously exposed. Consumer-grade routers often ship with insecure defaults, and many users never adjust them.
A 2022 BroadbandNow survey found that over half of households have never changed router settings, and nearly 90% still use default administrator credentials. This means millions of home offices operate with essentially unlocked digital doors.
The risks are not theoretical. Kaspersky reported more than 500 router vulnerabilities in 2021, including 87 critical flaws that could allow attackers full control.
Because routers now run complex operating systems, they offer multiple entry points, while most consumers continue treating them as simple plug-and-play devices. Criminals scan constantly for these weaknesses and exploit them within minutes of discovery.
Essential Router Security Steps
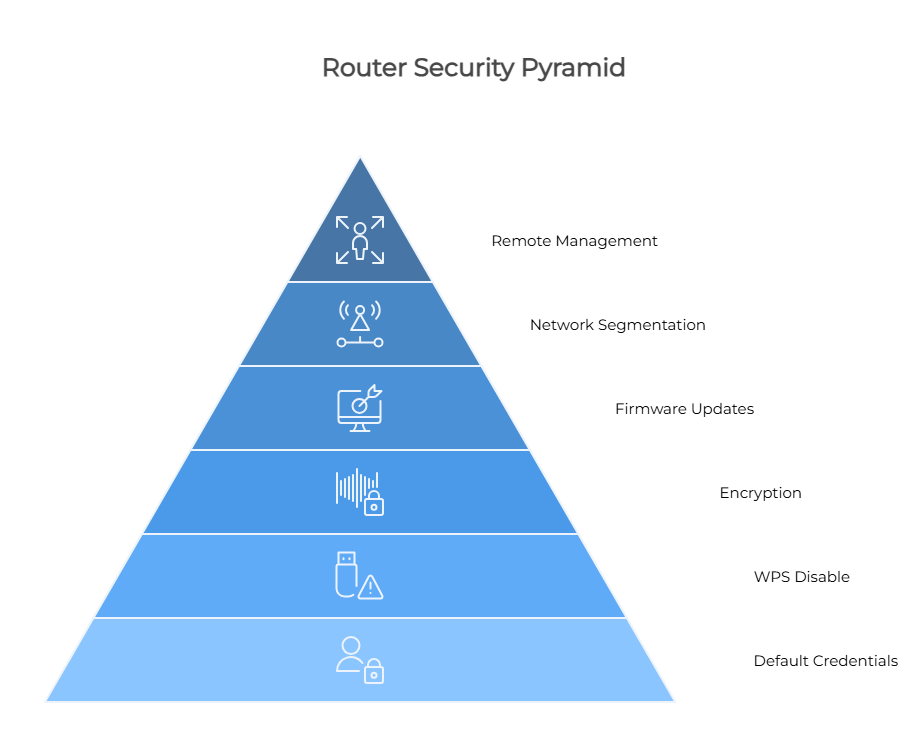
To secure your digital foundation, focus on the basics that most users overlook:
- Change default administrator credentials immediately.
- Disable WPS (WiFi Protected Setup), which remains widely exploitable.
- Use WPA3 encryption or at least WPA2 with long, complex passphrases.
- Enable automatic firmware updates to patch vulnerabilities quickly.
- Segment your network so work devices operate separately from personal ones.
- Turn off remote management unless absolutely necessary.
Network segmentation is especially critical. By placing your laptop on a dedicated work network, you prevent a compromised device – like a smart TV infected through a streaming app – from granting attackers access to sensitive business data. Many professionals working with Batten Home Security start with segmentation as their first line of defense.
VPN Protection for Remote Work
A Virtual Private Network (VPN) strengthens home office security by creating encrypted tunnels between your devices and the internet.
For remote professionals, consumer-grade VPNs fall short. Business-grade solutions available through Batten’s marketplace include kill switches that cut connections if the VPN drops, DNS leak protection to prevent exposure, and split tunneling to separate business from personal traffic.
Together, these features transform a VPN from a simple privacy add-on into a critical security tool for protecting both business operations and family data at home.
Identity and Access Management
Password security has become one of the biggest challenges for remote workers. AAG IT Support reports that phishing is the most common form of cybercrime, with an estimated 3.4 billion spam emails sent daily. Remote workers are three times more likely to be targeted, which makes strong authentication essential.
The average person now manages more than 100 passwords. Yet, 32.4% of employees admit they could fall victim to phishing without proper training. Password reuse compounds the problem. When a single account is breached, attackers use those same credentials across dozens of platforms through credential stuffing attacks. This chain reaction can compromise both professional and personal accounts within hours.
Modern password managers from Batten’s cybersecurity bundle solve this by creating unique, cryptographically secure passwords for every login.
They synchronize encrypted vaults across devices while using zero-knowledge architecture, meaning even the provider cannot see your credentials. Added features like breach monitoring and secure password sharing give both families and businesses a safer way to manage access. Find out more about the best password managers here.
Multi-Factor Authentication Evolution
Relying on SMS-based codes for multi-factor authentication (MFA) is no longer safe, as SIM swapping continues to expose users.
Egress found that over 84% of phishing attempts bypassed DMARC protections, showing that email checks alone cannot stop attackers. Stronger methods are now available, including authenticator apps and hardware security keys.
These devices use cryptographic protocols that resist phishing, ensuring credentials cannot be intercepted or cloned. For remote professionals, adopting hardware-based MFA is one of the most effective upgrades for identity security.
Data Protection Strategies
Remote work has scattered sensitive data across devices, cloud platforms, and physical media, creating multiple breach points. IBM reports that 40% of breaches involve data spread across different environments, while 46% expose customer personally identifiable information (PII). In most home offices, professional files are mixed with personal records, which increases the risk of accidental exposure or theft.
Encryption is no longer optional once data leaves controlled office environments. Full-disk encryption with BitLocker on Windows or FileVault on macOS should be standard for every device. This prevents lost or stolen laptops from turning into instant data breaches. Still, disk encryption alone is not enough. Files shared via email or stored in the cloud require additional safeguards such as encrypted transfer protocols and controlled access policies.
Cloud Storage Security
Cloud platforms are essential for collaboration, but they also remain high-risk. Studies show that 72% of data breaches involve cloud-based systems. Business-grade cloud storage helps mitigate this with features such as customer-managed encryption keys, giving organizations control even if the provider itself is compromised.
Data loss prevention (DLP) policies can also automatically detect and restrict sensitive information like credit card numbers or Social Security data from leaving secure environments.
Finally, every home office should follow the 3-2-1 backup principle: three copies of data, stored on two types of media, with one copy off-site. Since organizations take an average of 204 days to identify breaches and 73 more to contain them, backups must be tested regularly to ensure they can be restored when needed most.
Communication Security
Digital communications have become one of the most common attack surfaces for cybercriminals. UK government data shows that 85% of businesses reporting breaches in recent years experienced phishing attacks. The shift from in-person meetings to digital conversations has created permanent archives of sensitive information that attackers view as valuable entry points.
Email protection requires more than spam filters. Tessian research shows 92% of organizations have faced at least one business email compromise incident. These attacks often combine social engineering and open-source intelligence, using social media or corporate websites to craft convincing messages that bypass both technical controls and human judgment.
Video Conferencing and Collaboration Tools
Video conferencing platforms carry their own risks. Strategic discussions, financial planning sessions, and confidential updates are often recorded and stored in cloud archives with unclear access permissions.
These recordings can become liabilities if accounts are compromised.
Keepnet research highlights that cybercriminals frequently move across multiple channels to increase credibility.
After phishing emails, Microsoft Teams is the most common next vector, used in 30.8% of observed multi-platform attacks. This pattern shows why security controls must extend across all communication platforms, not just email.
Physical and IoT Security
Protecting a home office goes beyond digital safeguards. Physical security remains essential, especially since 57% of organizations have reported mobile device breaches tied to remote work. A stolen laptop carries far more than replacement costs – it can expose saved credentials, cached sessions, and even network configurations.
Smart devices add another layer of risk. The average U.S. household connects over 20 devices to its wireless network, yet many run outdated firmware or default credentials. These overlooked entry points can compromise an entire office environment. Alarmingly, 73% of users have never configured their router security, making IoT vulnerabilities even more pressing.
Physical Security Layers
Effective measures include positioning desks away from windows, using privacy filters during video calls, and securing doors with high-quality locks.
Cable locks for laptops, locked cabinets for sensitive files, and cross-cut shredders for document disposal further reduce exposure. Batten’s home security systems integrate smart locks, cameras, and environmental sensors with professional monitoring to deliver complete protection.
Family Safety Integration
Home office security must also account for family members sharing the same space and network. Children connecting for school, gaming, or social media can inadvertently expose vulnerabilities.
Teaching basic practices – avoiding suspicious links, creating strong passwords, and respecting workspace boundaries – helps protect both business data and family privacy.
Parental control solutions available through Batten’s marketplace strengthen these defenses by limiting risky downloads, filtering content, and restricting access to work devices. This ensures both business continuity and safe online habits for the entire household.
Building Your Security Checklist

Creating an actionable security checklist transforms overwhelming requirements into manageable tasks. Only 14% of SMEs have a cyber security plan, yet those with documented procedures experience significantly fewer incidents. Your checklist should prioritize high-impact improvements that can be implemented immediately.
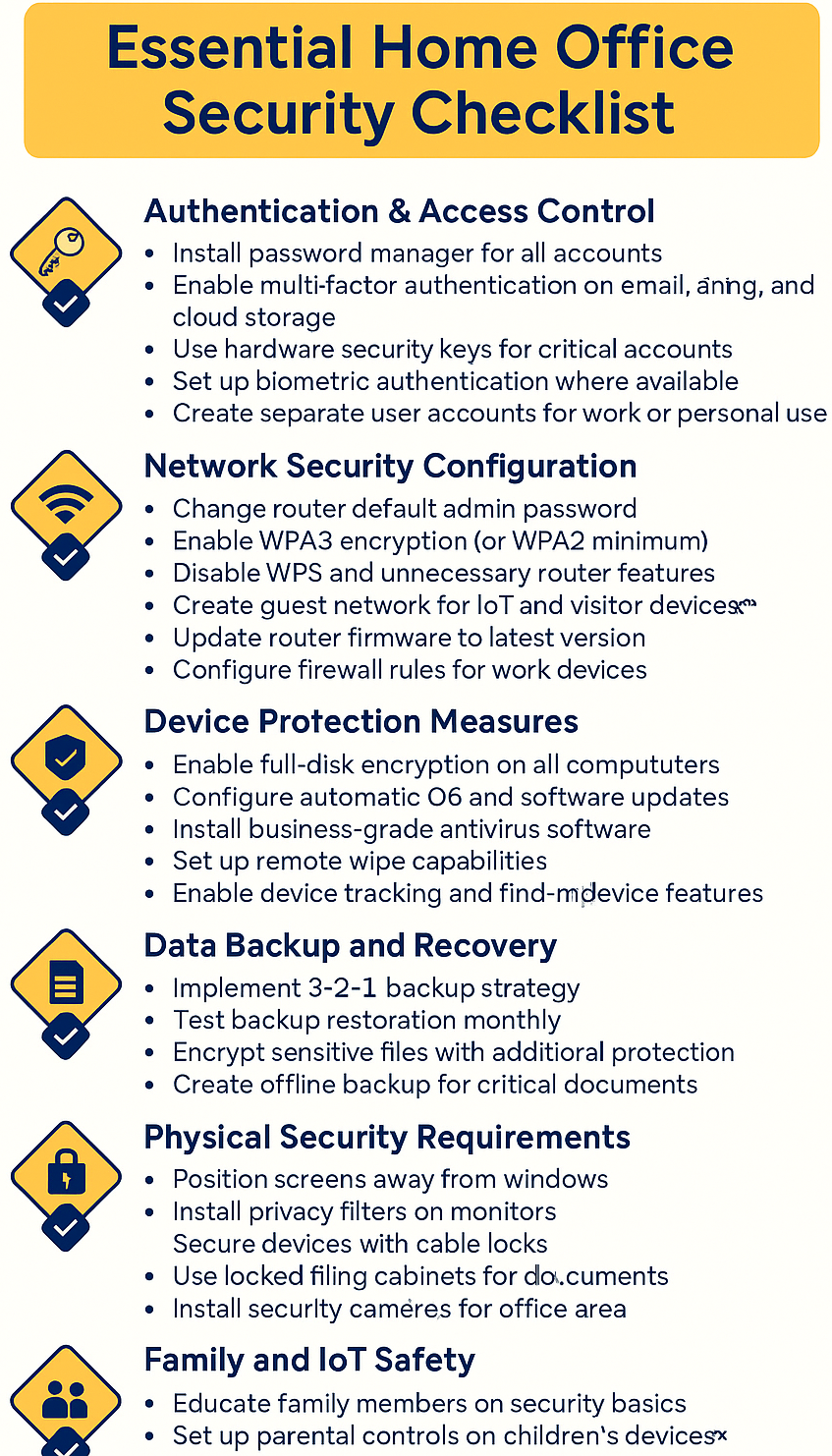
Essential Home Office Security Checklist
Authentication & Access Control
- Install password manager for all accounts
- Enable multi-factor authentication on email, banking, and cloud storage
- Use hardware security keys for critical accounts
- Set up biometric authentication where available
- Create separate user accounts for work and personal use
Network Security Configuration
- Change router default admin password
- Enable WPA3 encryption (or WPA2 minimum)
- Disable WPS and unnecessary router features
- Create guest network for IoT and visitor devices
- Update router firmware to latest version
- Configure firewall rules for work devices
Device Protection Measures
- Enable full-disk encryption on all computers
- Configure automatic OS and software updates
- Install business-grade antivirus software
- Set up remote wipe capabilities
- Enable device tracking and find-my-device features
Data Backup and Recovery
- Implement 3-2-1 backup strategy
- Test backup restoration monthly
- Encrypt sensitive files with additional protection
- Configure cloud storage security settings
- Create offline backup for critical documents
Physical Security Requirements
- Position screens away from windows
- Install privacy filters on monitors
- Secure devices with cable locks
- Use locked filing cabinets for documents
- Install security cameras for office area
Family and IoT Safety
- Educate family members on security basics
- Set up parental controls on children’s devices
- Update all smart home device firmware
- Change default passwords on IoT devices
- Review app permissions on family devices
Regular security reviews prevent degradation over time. Monthly checks should verify software updates, review connected devices, and test security controls. Quarterly deep-dives examine specific areas like account permissions or IoT device firmware. Documentation creates accountability and demonstrates due diligence for compliance requirements.
Emergency Preparedness
Security events demand fast, structured responses. IBM reports show that breaches resolved in under 200 days cost an average of $3.87 million, while those left unresolved beyond 200 days rise to $5.01 million. Remote workers face added risks, as isolation often delays detection and allows issues to escalate.
Warning signs include unexplained password resets, logins from unfamiliar locations, sluggish device performance, or coworkers receiving emails you never sent. With the average breach taking 277 days to identify and contain, recognizing these red flags early can dramatically reduce damage.
An effective incident response plan should cover immediate device disconnection, credential changes on secure systems, and use of pre-established communication channels. Batten’s emergency preparation resources provide structured playbooks for handling different types of incidents. Recovery should always be methodical, ensuring threats are fully removed before systems are brought back online.
Cost-Benefit Analysis
IBM research shows that organizations using security AI and automation save nearly $2.2 million per breach while detecting threats 98 days faster on average. While those numbers reflect enterprise environments, the principle applies equally to home offices and small businesses.
For remote workers, even modest improvements can yield outsized returns. Password managers cut off credential-based breaches, VPNs block man-in-the-middle attacks, and reliable backup systems guarantee continuity when incidents occur. The combined cost of these tools is typically less than a single day of downtime, making proactive investment a clear financial advantage.
Taking Action Today
Securing a home office is no longer optional for professionals balancing business responsibilities and family life. As remote work grows, the risks tied to unsecured networks, poor identity management, and unprotected devices also increase.
This guide showed how to build strong defenses, from network segmentation and VPN protection to password managers, multi-factor authentication, and physical safeguards. Cloud storage security, data backups, and incident response planning ensure resilience when breaches occur, while family education and IoT protection reduce hidden vulnerabilities.
Even modest improvements in small business security at home can prevent costly losses and protect sensitive data. Now is the time to take action – start implementing these steps today with Batten’s cybersecurity bundles, home monitoring solutions, and emergency resources.
Ready to secure your home office? Explore Batten’s comprehensive security solutions for complete protection. From cybersecurity tools to physical security systems, discover how to protect what matters most.
Essential Security Resources:
- Cybersecurity protection bundle for digital defense
- Home security hardware for physical protection
- Emergency preparation guides for incident response
Frequently Asked Questions
What’s the Average Cost to Secure a Home Office Properly?
Basic home office security can be achieved for $300-$800 annually. This includes a password manager ($30-60/year), business-grade VPN ($60-120/year), antivirus software ($50-100/year), and basic security hardware like door sensors and cameras ($150-400 one-time). Professional monitoring adds $20-50 monthly. Batten’s security bundles provide comprehensive protection starting under $500, combining physical and digital security tools.
Does My Homeowner’s Insurance Cover Work Equipment and Liability?
Most homeowner’s policies provide limited coverage for business equipment (typically $2,500 max) and exclude business-related liability claims. If clients visit your home office or you store expensive equipment, you’ll need additional coverage. Remote employees should verify their employer’s insurance covers home-based work injuries and equipment. Self-employed workers require separate business insurance for full protection. Check with your insurance provider about endorsements for home office coverage.
Can I Claim Home Office Security Expenses on My Taxes?
If you’re self-employed or run a business from home, security expenses are generally tax-deductible as business expenses. This includes security systems, cybersecurity software, locks, cameras, and monitoring services used primarily for business protection. W-2 employees working remotely cannot deduct these expenses under current tax law (2018-2025). Consult a tax professional for your specific situation and maintain receipts for all security-related purchases.
How Do I Secure My Home Office if Family Members Share My Devices?
Create separate user accounts with different permission levels on all devices. Use parental control software to restrict children’s access to work applications and files. Enable guest mode for family browsing sessions. Store work files in encrypted folders accessible only through your account. Consider purchasing a dedicated work device if handling highly sensitive data. Train family members on basic security awareness and establish clear device usage rules.
What’s the Difference Between Home Office Security for Employees vs. Business Owners?
Remote employees typically receive equipment and security tools from employers, with company IT support for configuration. Their employer’s business insurance usually covers equipment and liability. Business owners must purchase their own security infrastructure, maintain separate business insurance, and ensure compliance with industry regulations. They also face greater liability for client data breaches and need more comprehensive cybersecurity solutions including data loss prevention and professional liability coverage.
How Often Should I Update My Home Office Security Measures?
Review security settings monthly: check for software updates, verify connected devices, and test backups. Conduct quarterly deep reviews of account permissions, password changes for critical accounts, and IoT device firmware updates. Annual assessments should include replacing outdated equipment, updating emergency response plans, and reviewing insurance coverage. Stay informed about emerging threats through Batten’s preparation guides and security advisories.
What Immediate Steps Should I Take if I Suspect a Security Breach?
Disconnect affected devices from the internet immediately. Change passwords for all critical accounts from a clean device. Document everything: times, suspicious activities, error messages. Contact your IT department (employees) or cybersecurity professional (business owners). Preserve evidence before attempting fixes. Check financial accounts for unauthorized activity. File reports with appropriate authorities if data was compromised. Never pay ransoms without consulting law enforcement and security professionals first.
Sources
- The Number of People Primarily Working From Home Tripled Between 2019 and 2021
- IBM Report: Escalating Data Breach Disruption Pushes Costs to New Highs
- Home Router Security Risks: 2024 Survey Results and Solutions
- Router security report 2021 | Securelist
- The Latest Phishing Statistics (updated June 2025) | AAG IT Support
- Top Phishing Statistics for 2025: Latest Figures and Trends
- 110+ of the Latest Data Breach Statistics to Know for 2026 & Beyond
- Cyber security breaches survey 2025 – GOV.UK
- 2025 Phishing Statistics: (Updated August 2025) – Keepnet
- 7 Tips for Avoiding Remote Work Security Risks | Wrike
- 87 critical vulnerabilities discovered in routers in 2021
- 120 Data Breach Statistics for 2025
- How Long Will It Take To Recoup From a Data Breach?




